hackthebox.eu: Luke Walkthrough
Started with nmap scans. Found ports 21, 22, 80, 3000, and 8000 open. Also nmap indicated that anonymous FTP is allowed.
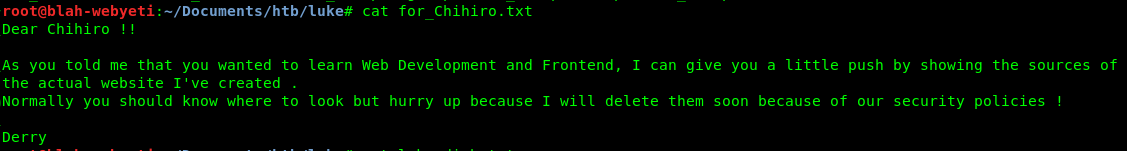
Connecting to FTP shows a couple of files and what could be a hint.
I then started running dirb and dirbuster scans against the web interfaces to see what I could find if anything. My searches were focused on port 80, 3000, and 8000. I used the common wordlist from dirb and the 1.0 directory list as well as setting both scans to be recursive.
Found some more login pages (or so I thought) on port 3000. This could be useful later.
Also found some interesting pages on port 80.
Port 8000 has a web interface with a login, but nothing else of note right now. I’ll have to take a look at this later if I find credentials.
After reading in the forums for a bit I found that this application uses Java Web Tokens for authentication. Web searching on JWT uncovered posts on Medium that seemed useful.
https://medium.com/prod-io/understanding-the-basics-of-node-js-99e01c5d844f
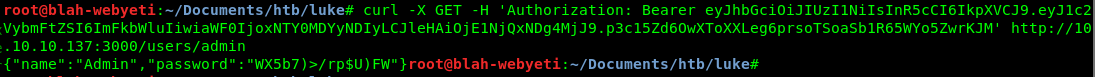
I also found a config file with a password in it. This file says the password is for root, but it’s a good idea to try this against other common accounts like admin. I admit that it’s a bit of a leap of logic, but that really does happen sometimes during real-world tests. That combined with a one-liner using curl from that last link got me some success.
Ok, so I have auth and a token. Now what to do with the token? My dirb results on port 80 showed other pages that could be used with a useful one-liner from the dev-bits article. This technique recovered more data out of the system. It turned out that not only admin (http://10.10.10.137/users/admin), but all the other users had pages that returned passwords. Now I have a bunch of credentials and I need to try in other locations. Back to the results of my initial recon. Eventually I made my way back to the auth required page (management) on port 80.
name":"Admin","password":"WX5b7)>/rp$U)FW"
name":"Derry","password":"rZ86wwLvx7jUxtch"
name":"Yuri","password":"bet@tester87"
name":"Dory","password":"5y:!xa=ybfe)/QD"
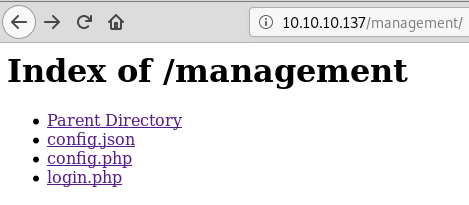
With these passwords I went to the http://10.10.10.137/management page and tried all of them to see if any would work. Authenticating with the user “Derry” got me into a directory with some other useful files.
Looking at the config.json I see a few other useful things that I think may be what I need.
It looks like there are some credentials here! The root:KpMasng6S5EtTy9Z credential set comes from config.json. I used that against the login page on port 8000. Success!
A couple of things look interesting to me right away, but I’ll go to File Manager and see what’s up.
I navigated through the files to /home/Derry/ and found user.txt
By clicking on the EDIT button I can see the flag and copy it out to submit. User owned. Now thinking about it, I logged in as root. Surely it can’t be that easy can it? I’ll navigate to /root and...
Apparently it can. That finishes owning the flags for this one.
Other Resources
There are some other great write-ups for this challenge. I’m going to start linking them at the bottom of my posts and checking them out myself. There’s almost always more than one way to do these things and once you’ve solved the problem, seeing other branches you didn’t take completes the picture.
IppSec’s excellent video - https://www.youtube.com/watch?v=gaBdfD4BGBo&t=32s
A really good writeup by 0xdf with a shell callback - https://0xdf.gitlab.io/2019/09/14/htb-luke.html