hackthebox.eu: Sauna Walkthrough
Today we’ll walkthrough a new easy Windows machine with some fun enumeration paths and good repetition of basics in testing found passwords and post-exploit enumeration.
As usual with Windows, there are a LOT of ports open. But I’ll start with the website. The SSL version of the site doesn’t seem to want to load so I started with the HTTP version. I found a few pages looking around manually and decided to run Cewl against the site to mine some possible usernames.
I saw a hint that this machine is similar to both Forest and Monteverde which was funny because I was already looking through my reports for these machines thinking it was probably similar. Reuse of techniques and tools is a big reason that this blog exists, making notes helps me remember things I’ve already done as well as helps me remember the details later. Keep this in mind as you go forward in testing, notes help.
After taking a look at the about page and messing with some permutations of likely usernames I got what I was looking for. Initially I tried just lastname, but then I expanded out to fullname, firstname.lastname, and first letter of firstname and lastname and that got it. I need to remember and use the usual common username conventions when testing this sort of thing.
Looks like the user fsmith has a Kerberos hash that doesn’t require authentication to pull. Now that I have this I should be able to try cracking it. Most of the time on HTB based on the machine submission rules heavy duty cracking isn’t required so John the Ripper and the rockyou wordlist should work.
I messed around with SMB shares a bit, but nothing there looked very interesting. Then I decided to just try Evil-WinRM shell since it’s worked well in the past.
Got on the machine as easy as you please and now I can go grab the user.txt. On to looking at root.
I commonly start Windows privilege escalation by running PowerUp by harmj0y. It’s an excellent tool and covers a lot of ground quickly so I can eliminate any rabbit holes. I ran a Python SimpleHTTP Server on my attacking host and used certutil.exe to pull the file across.
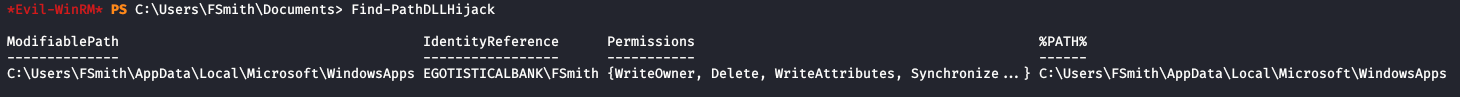
After getting PowerUp on the machine I ran all checks and see one possible avenue of targeting wlbsctrl.dll. Time to learn more about this attack path and determine if it’s effective on this machine.
I also verified this path via PowerSploit’s Find-PathDLLHijack module. I was never able to get this DLL Hijack working so maybe it doesn’t work or I just didn’t have the right technique in this case.
This may still work, but I’m going to do some more recon to see what I can find.
lookupsid.py EGOTISTICAL-BANK/FSmith:Thestrokes23@10.10.10.175
Impacket v0.9.20-dev - Copyright 2019 SecureAuth Corporation
[*] Brute forcing SIDs at 10.10.10.175
[*] StringBinding ncacn_np:10.10.10.175[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-2966785786-3096785034-1186376766
498: EGOTISTICALBANK\Enterprise Read-only Domain Controllers (SidTypeGroup)
500: EGOTISTICALBANK\Administrator (SidTypeUser)
501: EGOTISTICALBANK\Guest (SidTypeUser)
502: EGOTISTICALBANK\krbtgt (SidTypeUser)
512: EGOTISTICALBANK\Domain Admins (SidTypeGroup)
513: EGOTISTICALBANK\Domain Users (SidTypeGroup)
514: EGOTISTICALBANK\Domain Guests (SidTypeGroup)
515: EGOTISTICALBANK\Domain Computers (SidTypeGroup)
516: EGOTISTICALBANK\Domain Controllers (SidTypeGroup)
517: EGOTISTICALBANK\Cert Publishers (SidTypeAlias)
518: EGOTISTICALBANK\Schema Admins (SidTypeGroup)
519: EGOTISTICALBANK\Enterprise Admins (SidTypeGroup)
520: EGOTISTICALBANK\Group Policy Creator Owners (SidTypeGroup)
521: EGOTISTICALBANK\Read-only Domain Controllers (SidTypeGroup)
522: EGOTISTICALBANK\Cloneable Domain Controllers (SidTypeGroup)
525: EGOTISTICALBANK\Protected Users (SidTypeGroup)
526: EGOTISTICALBANK\Key Admins (SidTypeGroup)
527: EGOTISTICALBANK\Enterprise Key Admins (SidTypeGroup)
553: EGOTISTICALBANK\RAS and IAS Servers (SidTypeAlias)
571: EGOTISTICALBANK\Allowed RODC Password Replication Group (SidTypeAlias)
572: EGOTISTICALBANK\Denied RODC Password Replication Group (SidTypeAlias)
1000: EGOTISTICALBANK\SAUNA$ (SidTypeUser)
1101: EGOTISTICALBANK\DnsAdmins (SidTypeAlias)
1102: EGOTISTICALBANK\DnsUpdateProxy (SidTypeGroup)
1103: EGOTISTICALBANK\HSmith (SidTypeUser)
1105: EGOTISTICALBANK\FSmith (SidTypeUser)
1108: EGOTISTICALBANK\svc_loanmgr (SidTypeUser)
Found some more users to take a look at.
Doing some more enumeration I found another useful item in the Winlogon registry key.
So I can now run some of this against SMB using the Metasploit smb login auxiliary script and see if I have more username and password combinations.
The user HSmith is interesting, but can’t login remotely so that seems a dead end. The svc_loanmgr user can login remotely and we may be able to do more… time to research some more.
I started working my way through the Impacket scripts and did not succeed using GetADUsers, GetNPUsers, or mimikatz modules but then I went back to secretsdump and had some success.
I have some hashes so my first instinct is to try to pass them. I tried pth-winexe but that didn’t work.
Back to Impacket as I think I can pass hashes via that framework as well. I chose WMI just from personal experience finding that WMI sometimes works where PSExec and other tools fail.
Success! Now to go get my loot.
Done! Thanks to egotisticalSW (https://www.hackthebox.eu/home/users/profile/94858) for a fun machine with some interesting techniques.
Items learned or remembered:
Impacket kerberos abuse modules
Reg query for saved Winlogon credentials
Always circle back to your usernames and passwords when you find more
Certutil to pull files across is quite reliable in my experience
Windows find does not work under Powershell… that is annoying
Secretsdump.py and pulling hashes
Using pass the hash with Impacket scripts to gain a shell